Speed and Capital Efficiency
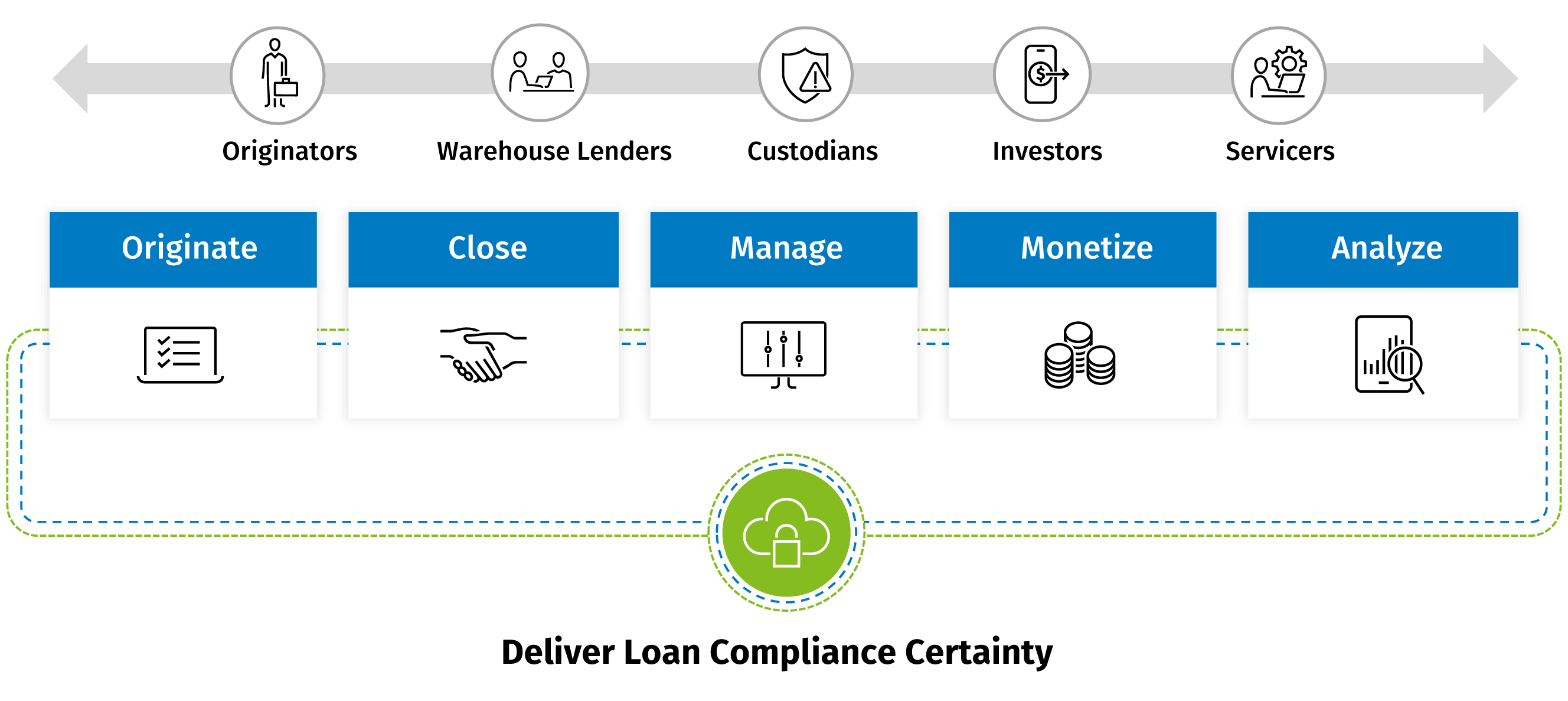
eOriginal accelerates the rate at which digital financial assets are closed, collateralized, securitized and sold into the secondary market – fueling greater capital efficiency and leverage.
eOriginal accelerates the rate at which digital financial assets are closed, collateralized, securitized and sold into the secondary market – fueling greater capital efficiency and leverage.